IT asset management (ITAM)
What is IT asset management (ITAM)?
IT asset management (ITAM) is a set of business practices that combines financial, inventory and contractual functions to optimize spending and support lifecycle management and strategic decision-making within the IT environment. ITAM is often a subset of the IT service management (ITSM) process.
An IT asset is classified as any company-owned information, system or hardware used in business activities. The IT asset management process typically involves gathering a detailed inventory of an organization's hardware, software and network assets and then making informed business decisions about IT-related purchases and redistribution.
ITAM applications are available to organizations to assist in the ITAM process. These applications can detect the hardware, software and network assets across an organization and then capture, record and make the data available. Some of these applications integrate ITAM with the service desk, keeping user and access information together with incidents and requests.
Why ITAM is important
ITAM is about more than creating an asset inventory. It's about continually using the captured asset data to maximize returns, minimize risk and drive increased business value. By avoiding unnecessary asset purchases and making the best use of current resources, IT asset managers can cut software licensing and support costs, eliminate waste and improve efficiency.
This article is part of
What is desktop management and how does it work?
ITAM also helps increase the company-wide understanding of IT's business value, improves communications and understanding between IT and other departments, enforces compliance with cybersecurity policies and regulatory requirements, improves productivity through technical support, and limits overhead costs of managing the IT environment.
What are the types of IT asset management?
The four primary types of ITAM purchase options include the following:
Hardware and software asset management
In this type of strategy, IT has a platform that focuses solely on delivering the management of IT hardware such as endpoint devices, mobile devices, servers, workstations and any software in use.
Cloud asset management
A cloud asset management tool focuses on supporting the management of cloud asset services from Amazon, Microsoft, Google or other cloud service providers.
Digital asset management
Asset management tools are mainly used by organizations that manage digital content to track licensing, formats, metadata and other attributes. These tools provide features and functionality not found in other products.
Fixed asset management
These tools track assets including desks, printers, networking cabinets, server room AC units and any other fixed IT assets within the environment.
Benefits of ITAM
There are numerous benefits of using an ITAM tool for IT assets, including the following:
- maintaining a centralized location for all asset information for IT;
- having better visibility into where assets are and detailed information on them;
- reducing risks;
- staying organized with all the different asset categories and reporting on them; and
- eliminating waste with duplicate purchase of assets.
ITAM best practices
The successful implementation of ITAM results from proper planning and a few other considerations, including the following:
- determining what type of tool would address the current needs for asset management;
- defining standard operating procedures for asset tracking, documentation in the system and how to use the system;
- creating a consistent tracking method to ensure that all relevant assets are accounted for;
- performing frequent audits of asset management by reviewing and updating existing assets based on a schedule; and
- having the ability to track critical data such as expiration dates, purchase dates, vendor contact information and other relevant details.
ITAM tools
Many options exist, and some enterprise-ready ITAM tools include the following:
- ManageEngine AssetExplorer
- Asset Panda
- GoCodes
- Ivanti IT Asset Management Suite
- ServiceNow
- SysAid
- BMC Track-It!
Effectively managing IT assets can also improve visibility and control of IT assets and help swiftly identify and replace stolen hardware and software components. ITAM can support other ITIL processes by providing accurate information about the assets affected by an incident, problem or change. ITAM also makes organizations more agile by allowing quicker and more accurate migrations, upgrades and company-wide changes.
IT asset and configuration data can be critical in the aftermath of natural disasters and other unexpected events. Proper ITAM can help leaders quickly identify the effects of such events and more confidently make decisions to restore services.
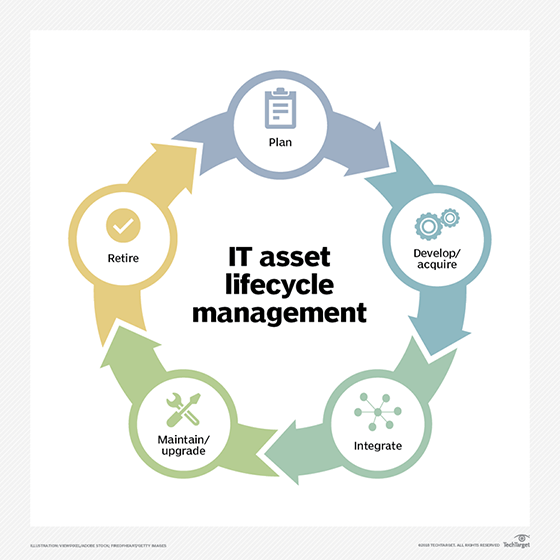
IT asset management processes
ITAM is a continual and systematic process, so the asset lifecycle concept helps structure activities and support decision-making. The cycle starts with strategic planning across the organization to determine what assets are needed, how to procure them, the specific ways they'll be used and how they'll be funded. This often includes total cost of ownership (TCO) estimates and a cost-benefit analysis of alternatives.
Next is the procurement phase, in which organizations build, purchase, lease or license the assets they need. Following procurement is the integration phase, during which the assets are installed and introduced into the IT ecosystem. This includes properly integrating the assets with other components, establishing support and operations processes and specifying user access.
Maintaining and upgrading the assets is the next phase of the IT asset lifecycle. To maximize the value of the asset and extend its life -- as well as mitigate risks and reduce support costs -- maintenance, repair and extensive overhauls may be necessary.
Once the asset has reached the end of its useful life, the last phase is asset retirement and disposal. That often includes "transitioning users to other resources, updating asset records, canceling support agreements, terminating license renewals and initiating the planning for replacement assets," according to Freshservice, a cloud-based service desk and ITSM system.
ISO standards for ITAM
The International Standards Organization (ISO) has established an official set of standards for ITAM. This family of standards, ISO 19770, consists of five major parts and was updated in 2017. Below are the five parts and what they entail, as encapsulated by Freshservice.
- ISO/IEC 19770-1. A process framework that outlines best practices for ITAM in an organization. It provides organizations a way to prove that they're performing ITAM per the standards that satisfy corporate governance requirements and support IT service management activities.
- ISO/IEC 19770-2. A data standard for software identification tags. This enables organizations to identify software deployed on a given device.
- ISO/IEC 19770-3. A data standard for detailing the entitlements and rights associated with a piece of software and the method for measuring license or entitlement consumption.
- ISO/IEC 19770-4. A measurement standard that allows for standardized reporting of resource utilization. This standard is especially important when managing complex data center licenses and cloud-based software and hardware.
- ISO/IEC 19770-5. Provides an overview of the ISO-defined ITAM standards and associated vocabulary.






