Open Container Initiative
What is the Open Container Initiative?
The Open Container Initiative (OCI) is a collaborative project hosted under the Linux Foundation that is designed to establish common standards for container formats and runtimes.
The OCI is vendor neutral and has an open governance structure. The project's core goals are to ensure standards for containers and future container platforms that preserve the flexible and open nature of containers.
Open Container Initiative aims and projects
The formation of the OCI was driven by rapidly rising interest in container-based virtualization, particularly as a way to increase application portability across multiple environments.
Specifically, the OCI is guided by the following principles:
- Containers should not be bound to a specific client or orchestration stack.
- Containers should not be tightly associated with any particular vendor.
- Containers should be portable across a wide variety of operating systems, hardware and architectures.
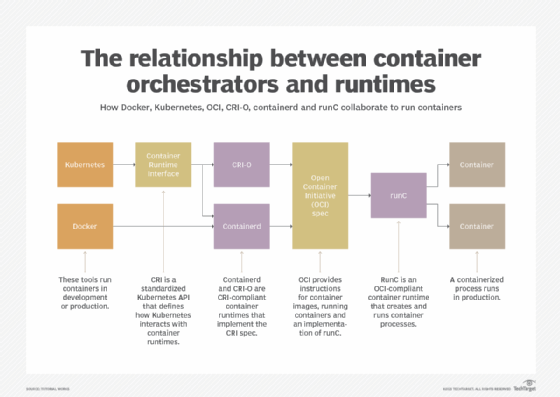
The OCI project currently encompasses three container specifications: the Runtime Specification, the Image Specification and the Distribution Specification.
History of the Open Container Initiative
The OCI was first unveiled as the Open Container Project at DockerCon on June 22, 2015. The project was later renamed as the Open Container Initiative.
The Open Container Initiative has support from a long list of prominent companies, with founders including Amazon, CoreOS, Docker, IBM, Goldman Sachs, Google, Microsoft and VMware. However, the project remains independent from any one commercial organization.
Docker was especially pivotal in founding the OCI. To launch the project, Docker donated draft specifications and much of the existing code for Docker's image format and container runtime.







