What is change control?
Change control is a systematic approach that includes the various steps needed to process changes made to a product or system.
Completing change control methodically is part of a change management process. The purpose of change control and change control management is to ensure that no unnecessary changes are made, all changes are documented, services are not disrupted unnecessarily, and resources are used efficiently. Within IT, where processing changes is a daily activity, change control is a component of change management.
The change control process is usually conducted as a sequence of steps resulting from the submission of a change request. Typical IT change requests include adding features to software applications, installing patches, and upgrading network equipment or systems.
How does the change control process work?
The following is an example of a six-step process for a software change request:
- Documenting the change request. The client's change request or proposal is categorized and recorded, along with informal assessments of the importance of that change and the difficulty of implementing it.
- Formal assessment. This step evaluates the justification for the change and the risks and benefits of making or not making the change. If the change request is accepted, a development team will be assigned. If the change request is rejected, that is documented and communicated to the client.
- Planning. The team responsible for the change creates a detailed plan for its design and implementation, as well as for rolling back the change should it be deemed unsuccessful.
- Designing and testing. The team designs and tests the program for the software change. If the change is deemed successful, the team requests approval and an implementation date.
- Implementation and review. The team implements the program and stakeholders review the change.
- Final assessment. If the client is satisfied with the implementation of the change, the change request is closed. If not, the project is reassessed, and steps might be repeated.
The following diagram shows a visual representation of the change request process.
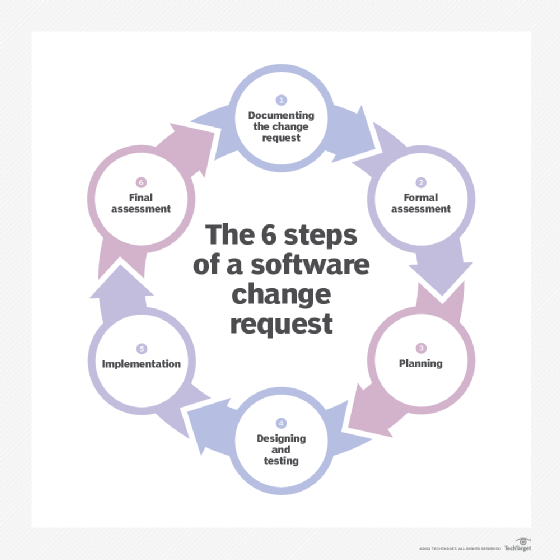
The basic change control process is simple. Anyone can submit a change request. Once the request has been written and submitted, it is reviewed by the change management team. If approved, it might be analyzed further, or it can go directly to the change control board (CCB). Assuming the proposed change gets approved for processing, it goes through multiple steps that can include design, engineering, prototyping, hardware and software selection, acceptance testing, rollout into production and follow-up before the request can be closed.
The basic components of a typical change request are typically universal across industries, and include the following:
- The date of the request.
- The name, role and department of the person making the request.
- A description of the change being requested.
- The reason or justification for the change.
- The impact that the change will have on processes, quality and budget.
- Priority or the importance of the request.
- Action plan for implementing the request; this is optional.
- Approval and authorization for the request.
Who uses change control?
In a typical IT department, a change control board examines the proposed changes, assesses viability, recommends approval or rejection, and conducts subsequent reviews as the change progresses to completion. IT employees can be assigned to the CCB and also to one or more change management teams.
IT department employees are the most likely to submit change requests since they work with systems and networks daily. Any proposed change is first discussed with management. If the issue has merit, the employee prepares a change request signed by a manager and submits it to the change management team.
Company employees can also propose a change. Initial contact is with the help desk to establish a ticket for tracking. Then the request is queued for review by the change management team, which provides an initial review and assessment. The team might be authorized to reject a request without sending it to the CCB. If the team approves the request, a formal change document is prepared with a detailed description as specified in the change management policy. When the CCB meets, its members can discuss the request. If more information is needed, the request will be returned to the requestor. The updated request is then sent to the CCB for further discussion and to decide on the changes.
When to implement change control
Change control is typically a good idea when one of the following conditions arise during project planning:
- The scope of a project has changed.
- The timeline of a project has changed.
- The project budget has been revised.
- Quality requirements for the project have been modified.
- Potential risk has increased or decreased, changing conditions.
- Compliance requirements must be considered.
- Technology or processes involved in executing the project have changed.
- Errors must be corrected.
Change control and change management for auditing
From an audit perspective, the change management process is a collection of specific controls, including change control, each of which contributes to the completion of a change. While the change process is typically depicted as a series of steps, the steps can also be considered controls for audit review.
The following diagram depicts a change management process and several of its controls.
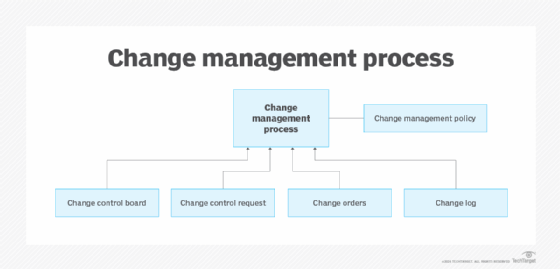
The diagram includes a change management policy, which specifies the various controls as indicated, such as initiating the CCB. Each control might have numerous subprocesses as part of the overall control. The presence of a policy is an important audit control.
Change control in project management
Change control is an important part of project management in IT and non-IT areas -- including manufacturing and pharmaceuticals -- and can be a formal or informal process. Project managers examine change requests to determine their potential effect on the project or system. Effective change control processes are critical for incorporating necessary changes while ensuring they do not disrupt other project activities or delay progress.
Each potential change must be evaluated in relation to its potential effect on the following:
- Scope of the project.
- Schedule of progress and milestones.
- Costs of additional labor and other resource requirements.
- Quality of the completed project, as excessive quantities of work can lead to rushed work, resulting in a higher likelihood of defects.
- Human resources, as change requests might require additional labor or specialized skills.
- Risk, as even minor changes can have a domino effect on the project, leading to potential logistical, financial or security risks.
- Impact on the business, such as creating more value for the company or improving a process that saves money and resources.
- Procurement of materials, labor, skills and other necessary project resources.
- Stakeholders -- including project managers, executives, company owners, vendors, team members or investors -- who might voice their support or push back on a project.
Within IT, change management and project management often operate in parallel. For example, a project's outcome, such as a scope change, could necessitate a change request. Both activities are essential tools for successfully managing an IT department.
The following are some use cases for change control in project management:
- Pharmaceutical industry. This might include adjusting the ingredients and composition of medicines or implementing improvements and adjustments in synthesis processes.
- Software development. This could include project codebase adjustment, updates to user interface and implementation of new security features.
- Construction. This might include new safety protocols and substitution of materials.
- Manufacturing. This could include implementing new compliance requirements, upgrades to quality control processes or adopting new employee safety standards.
Benefits of change control
Effective change control can provide the following potential benefits for projects in almost any industry:
- Better cost and risk avoidance.
- Lower risk associated with each individual change.
- Reduced amount of time needed for changes.
- Completion of changes that help the company be more productive, save money, compete more effectively and boost its reputation.
- Better communications and teamwork among employees.
- Changes can be factored in with less disruption to project schedules, as requests will be considered and managed around the project timeline.
- Project managers will be informed about change needs in the planning phase and have time to consider possible courses of action.
Best practices for change control
Change control is one aspect of the many components of change management. The following are recommended actions to take when change control and a change management activity are in place:
- Establish a change management policy that addresses the full spectrum of change-related activities.
- Ensure continued senior management support for the change process.
- Consider using an automated change management system such as Guru, Wrike, ManageEngine ServiceDesk Plus, SysAid, Whatfix or WalkMe. Examine open source tools for potential cost savings.
- Establish companywide awareness of the change management process.
- Establish a change control board with members who are committed to a strong change management process.
- Develop change request forms; an automated system might have its own forms.
- Establish and regularly update a change control log providing details on all active change requests.
- Set up a database and archive of completed change requests that can be referenced as evidence for audit review.
- Periodically review the change process and update it as needed.
Many organizations develop their own change processes that address the above items. For example, the U.S. Food and Drug Administration has published its own change guidelines covering topics such as quality management, quality risk management, corrective and preventive actions, and the quality unit for evaluating change.
Task automation tools can help organizations save time and reduce risks for IT operations. Learn what types of IT automation tools can help operations teams manage multiple tasks.







